we are in zone.sd
has best engineer in both cyber security & information security our security operation center SOC is operate 24*7 with working best practices .

Because you can’t build a world-class security operations center (SOC) overnight no
matter how much money you are willing to invest, the task is more of a marathon than
a sprint. Creating a plan for incremental phases of implementation is critical to success.
But what goes into such a roadmap? What comes first and what next?

The goal of planning should be to execute regular incremental improvements based
on your completed gap analysis and to establish a series of prioritized milestones that
lead the organization toward optimized security and improved incident detection and
response. The gaps you uncover in that analysis can be translated into goals. Budget,
personnel and cultural constraints require that new processes and technologies be
implemented in stages.

Technology
RedSocks Malicious Threat Detection Solution Security invented a unique concept for detecting and fighting malware, and has developed an innovative new Solution based on this innovative thinking. Traditional network security tools mainly only monitor inbound Internet traffic (Sandbox, Firewalls, Anti-Virus, etc). The RedSocks Malicious Threat Detection Solution (MTD) focuses on monitoring outbound traffic to detect malicious behavior and breaches.
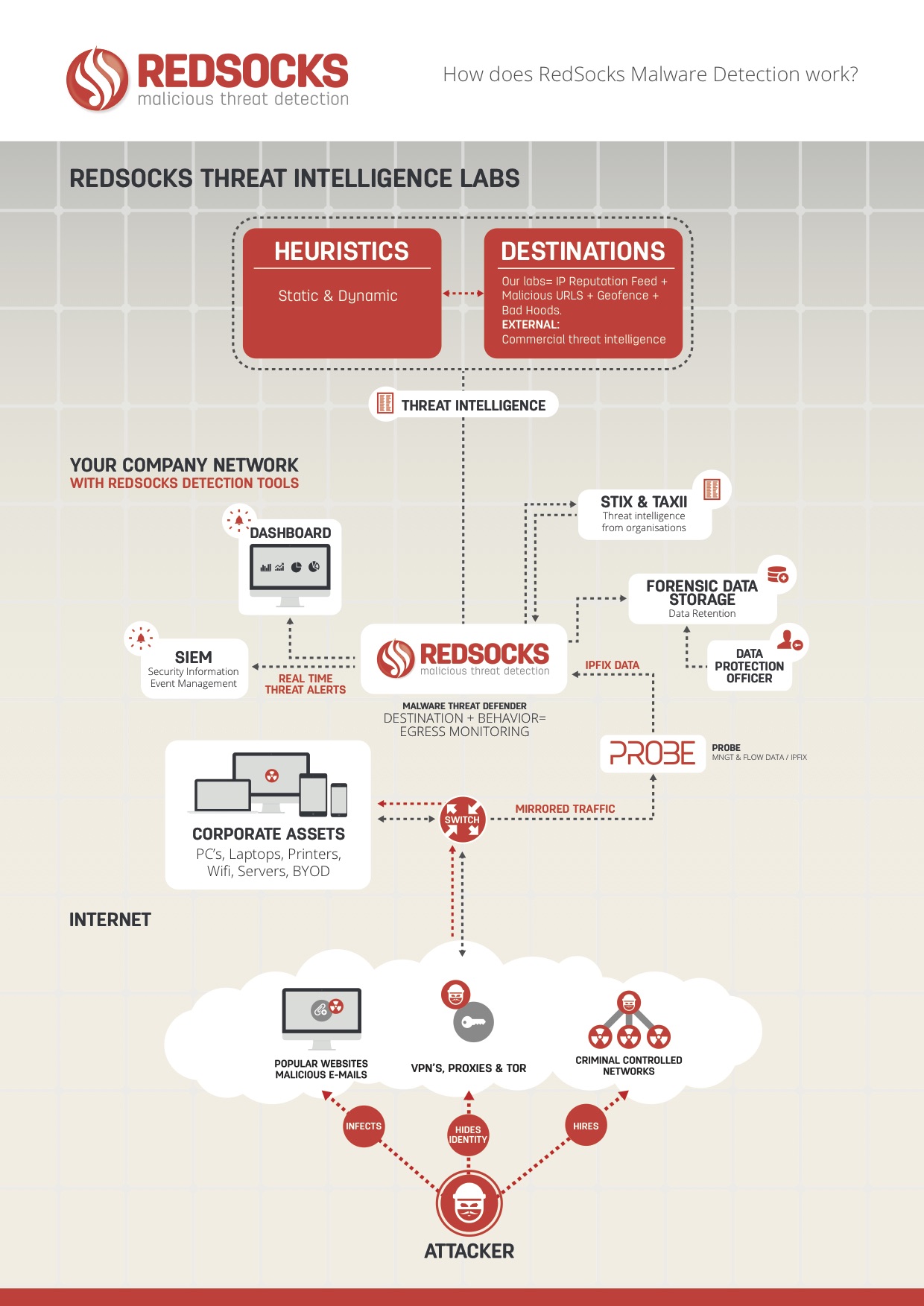
https://redsocks.eu/
An enterprisewide data collection, aggregation, detection, analytic and management
solution is the core technology of a successful SOC. An effective security monitoring
system incorporates data gathered from the continuous monitoring of endpoints (PCs,laptops, mobile devices and servers) as well as networks and log and event sources.
With the benefit of network, log and endpoint data gathered prior to and during the
incident, SOC analysts can immediately pivot from using the security monitoring system
as a detective tool to using it as an investigative tool, reviewing suspicious activities
that make up the present incident, and even as a tool to manage the response to an
incident or breach. Compatibility of technologies is imperative, and data silos are
bad—particularly if an organization has an existing security monitoring solution (SIEM,
endpoint, network or other) and wants to incorporate that tool’s reporting into the
incident management solution
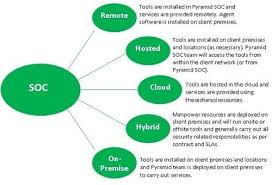
As you tackle the challenge of building a security operations center (SOC), your ability
to anticipate common obstacles will facilitate smooth startup, build-out and maturation
over time. Though each organization is unique in its current security posture, risk
tolerance, expertise and budget, all share the goals of attempting to minimize and
harden their attack surface and swiftly detecting, prioritizing and investigating security
incidents when they occur. Working within the constraints of your organization, while
pushing the boundaries and striving to achieve its critical security mission, your SOC
can be a critical and successful venture—and a key contributor to your organization’s
continuously improving security posture 

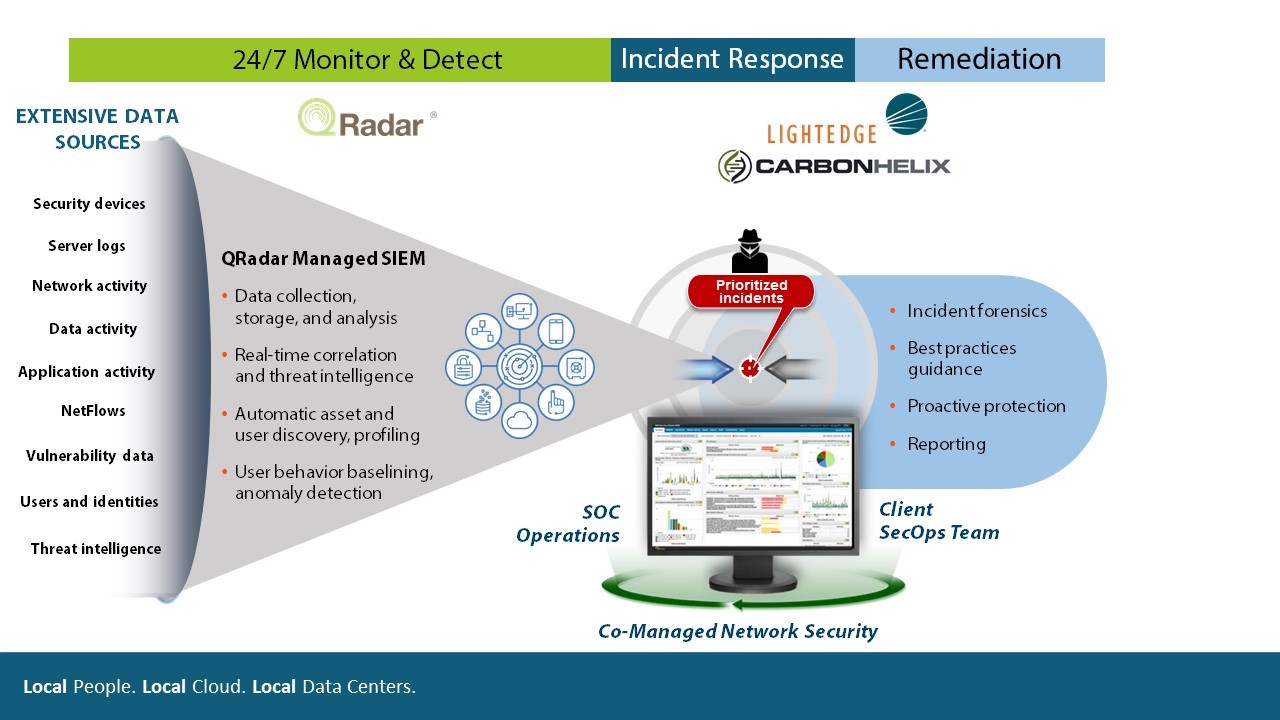
can be defined both as a team, often operating in shifts around the clock, and a facility dedicated to and organized to prevent, detect, assess and respond to cybersecurity threats and incidents, and to fulfill and assess regulatory compliance.

