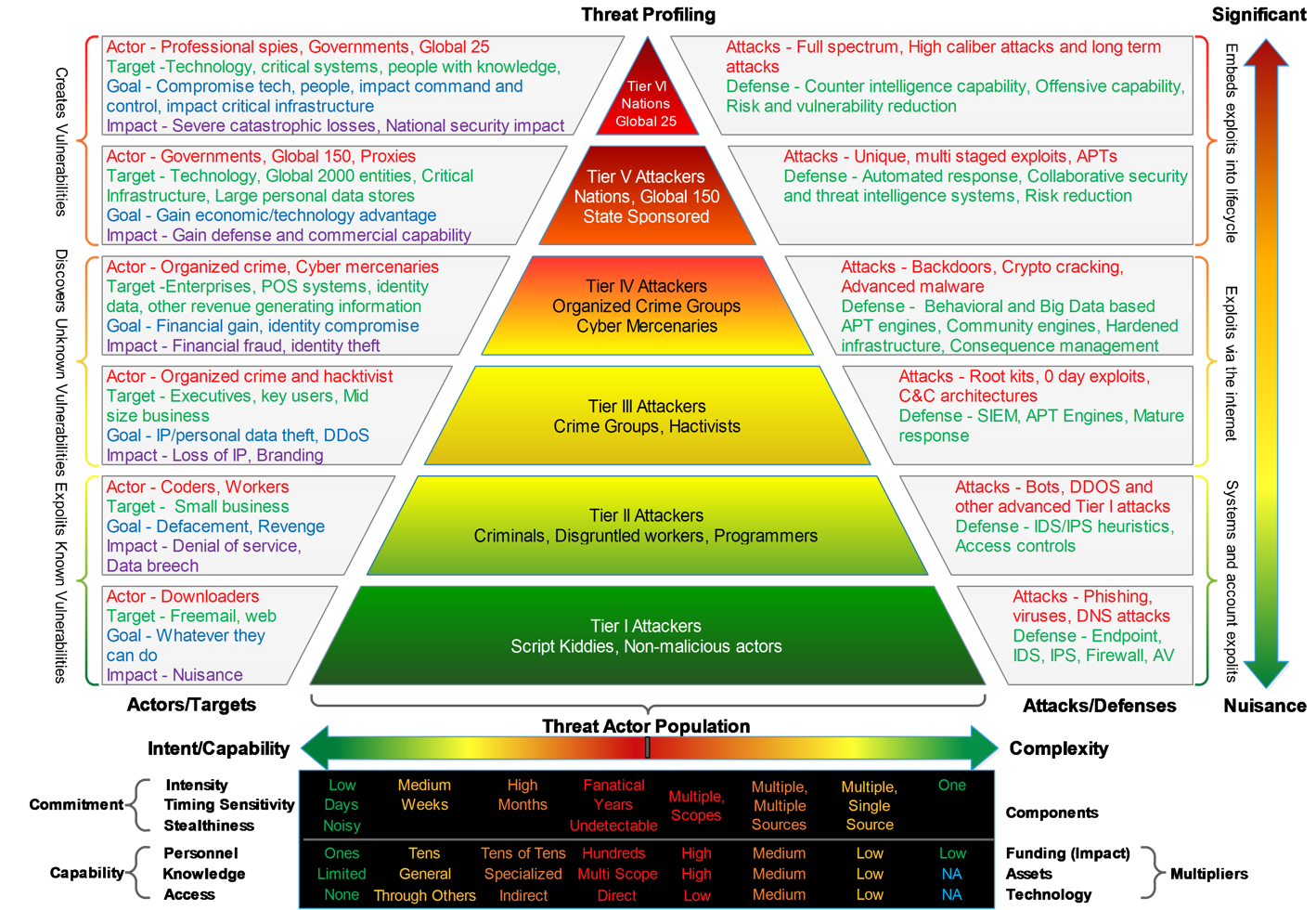
Soluation

Automate your Cyber Threat Analysis in real-time

Global Threat Intelligence with special focus
on Europe Africa and Asia
7 Malware Intelligence Lab
Heuristic engine detecting new,
previously unknown, threat
Behavioral Analysis
Detects Suspicious Network Traffic
Forensic security tool for GDPR Regulation
Data retention – Analyses suspicious traffic up to 36 month
Easy to deploy
Low TC
European Solution focused on Network Egress Monitoring

Easy to understand monitoring and alerting
Agentless – provides visibility into the security of employee- owned device
Non-intrusive
Operating System independent
Integrates with 3rd Party Security Tools such as SIE
Scalable Solution
IPFIX and Net Flow supper
STIX/TAXII support
encrypt your data be save
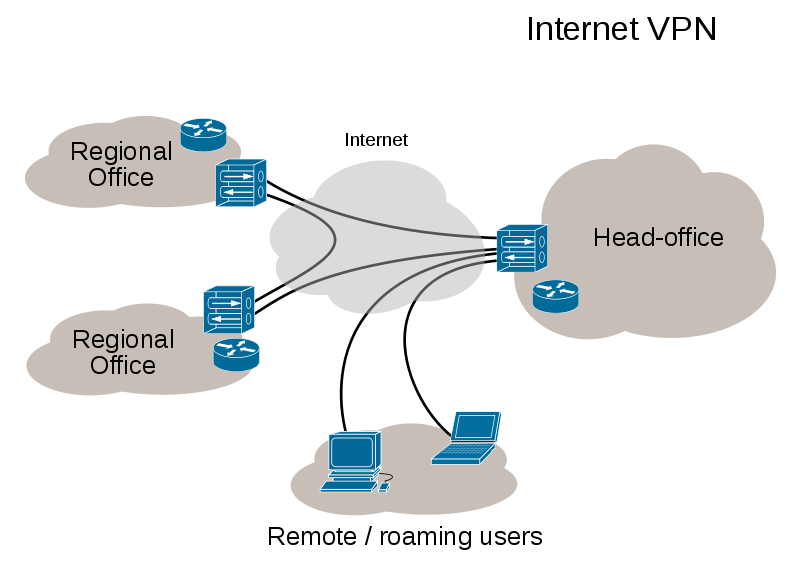
extends a private network across a public network, and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Applications running across the VPN may therefore benefit from the functionality, security, and management of the private network.[1]
our professional engineers will help you in building your VPNs may allow employees to securely access a corporate intranet while located outside the office. They are used to securely connect geographically separated offices of an organization, creating one cohesive network. Individual Internet users may secure their transactions with a VPN, to circumvent geo-restrictions and censorship, or to connect to proxy servers for the purpose of protecting personal identity and location in order to stay anonymous on the internet. However, some Internet sites block access to known VPN technology to prevent the circumvention of their geo-restrictions. Therefore, many personal use VPN providers have been developing technologies to bypass the blocking of proxies.
A VPN is created by establishing a virtual point-to-point connection through the use of dedicated connections, virtual tunneling protocols, or traffic encryption. A VPN available from the public Internet can provide some of the benefits of a wide area network (WAN). From a user perspective, the resources available within the private network can be accessed remotely
PCI POINT-TO-POINT ENCRYPTION (P2PE)™ SOLUTIONS
This listing is a resource for merchants and acquirers to use in selecting a PCI Point-to-Point Encryption (P2PE) Solution.
For information regarding the PCI P2PE program, for our document library.
Each PCI P2PE Solution has an associated P2PE Implementation Manual which is provided by the Solution Provider and contains details of all P2PE Applications and other software used in the Solution
