Virtualization & clouds
Cloud Computing
is the fundamental change happening in the field of Information Technology. It is a representation of a movement towards the intensive, large scale specialization.
Virtualization
is the key component of cloud computing. With the use of virtualization, cloud computing brings about not only convenience and efficiency benefits, but also great challenges in the field of data security and privacy protection. For example, it maybe bind different tenants’ virtual resources to the same physical resource, then the user data will be accessed by other users. To solve this problem, the paper analyses and discusses several ways to improve the safety of cloud computing.
CLOUD HOSTING PLATFORM
Our in-house built hosting platform is based on SSD drives and the ZFS file system, which is a guarantee for maximized site speeds, reinforced security and service scalability. Your and your customers’ sites will be in safe hands with us 24/7/365.
Based on the users’ needs and suggestions over the years, we have built a load-balanced web hosting platform, which breaks the common cPanel industry pattern and delivers a much better online experience to site visitors.
Learn more about the 3 main advantages of our custom-built hosting platform.
MAXIMIZED SITE SPEEDS
Thanks to a well-thought-out server configuration, our platform allows websites to load much faster compared with a regular hosting platform. Here are the main components that ensure the ultimate website browsing experience

SSD We use SSD drives instead of HDDs, since they are based on an innovative storage technology, which allows for faster data access and site loading. Tests have shown that a site hosted on an SSD performs a few times faster than a site hosted on a HDD.DATA Thanks to the ZFS LZ4 compression algorithm that we use to store content, data reading/writing on our hosting platform is a lot faster. This means that sites will be delivered faster to the public compared with the popular EXT4-based cPanel hosting platform.PLATFORM We have built a platform where the server workload is distributed between a few machines instead of just one, which accelerates the processing of server requests significantly. This way mails will go through faster, web applications will perform faster and sites will load faster
DATA CACHING
We cache frequently accessed site content in the server RAM so that future requests for the cached data will be processed faster. Also, we deploy servers with large amounts of RAM to make sure that bigger chunks of site content are cached efficiently as well.
WEBSITE ACCELERATORS
We’ve included various Control Panel tools, which will help users give an extra boost to their sites and apps. Memchached is perfect for traffic-heavy, data-base-driven websites like large e-stores, busy blogs, etc.; Varnish – for content-heavy sites with not-so-often-updated pages; and Node.js – for speeding up data-intensive, real-time apps.
A CUSTOM-BUILT NETWORK FOR FASTER ACCESS
We have built a load-balanced internal network, so as to boost the communication between the different servers. Also, our data centers have access to main internet backbones to ensure lightning-fast connectivity.
REINFORCED SITE SECURITY
Thanks to the extra security measures that we’ve take to shield our custom configuration, your sites will be protected from all types of common and ‘modern’ online threats, including DDoS attacks.
Here is a glimpse at the main security assets of our cloud hosting platform:

THE MODSECURITY ANTI-HACK FIREWALL
This Apache module will effectively prevent most URL forgery and brute-force attacks, as well as any website spamming attempts. It will automatically block all incoming requests that are flagged as insecure. It is kept constantly updated to prevent ‘up-to-date’ attacks.
AN ACCOUNT-BASED FIREWALL
The Outgoing Connections functionality integrated in the Control Panel will allow website owners to restrict the outgoing traffic and to prevent the leakage of sensitive data to external hosts, including malicious hacker scripts.

ANTI-VIRUS PROTECTION
Our servers are equipped with a powerful security system, which stops viruses, Trojans, worms and other malicious bugs aimed at disrupting websites and emails. All our servers are protected by a constantly running anti-virus software, which operates in the background and which does not affect the performance of the servers.

DATA CORRUPTION PROTECTION
The ZFS file system’s inbuilt checksum functionality, which is missing in the EXT4 file system used by most cPanel providers, ensures protection against silent data corruption. This way, if data gets corrupted on one of the disks in the RAID array, the system will be able to recognize the corrupted files and to recover the data from the unaffected disks.
GUARANTEED SERVICE UPTIME
Thanks to the overall service improvements to our network, we have managed to achieve and sustain a top-class system stability.
Here is a glimpse at the main stability assets of our cloud hosting platform:TOP-QUALITY SERVER HARDWARE COMPONENTS
To ensure the maximum possible uptime for your customers, we have set up our servers and whole internal network using enterprise-grade hardware only. Each hardware component is thoroughly tested before being used.
AN INTERNAL FIREWALL
All our servers are equipped with an internal firewall, which is constantly updated by our server administrators in order to react to possible server overload issues in a timely manner. This way, we can quickly block offending IPs or hacker attacks in real time, before they can unfold.
REDUNDANT POWER SUPPLY UNITS
Our network features redundant backup devices. This way, even in case of a hardware failure, we have a spare device ready to take over. We also have redundant power supply units, which can power our network in case of power supply problems.
BANDWIDTH REDUNDANCY
We avail of 2-4 Gbps of bandwidth, instead of the 1-gigabit-per-second network connection quota assigned to a server by default. This helps us avoid a network channel overload that could lead to loss of data packets and hence to downtime due to traffic overuse.
PROTECTIVE SERVICE LIMITS
To avoid peak memory usage during script execution, we’ve set certain limits. For example, a client cannot have more than 1000 processes running at a time, since this might seriously disturb their server’s performance.
COMPREHENSIVE CPU USAGE AND SYSTEM LOAD STATS
These will help users track the performance of their sites and applications in real time and take timely measures to avoid any possible service disturbances.
We are a Managed IT Support and Cloud Services Platform with World-Class Security and a Fanatical Support Staff. We are one of the industry’s only channel-exclusive IT Management Platforms.
Whether you need on-premise support or cloud-based assistance, we can help. We provide managed IT support, managed security solution, cloud and backup services for servers, desktops, mobile devices and other endpoints
Cloud Infrastructure 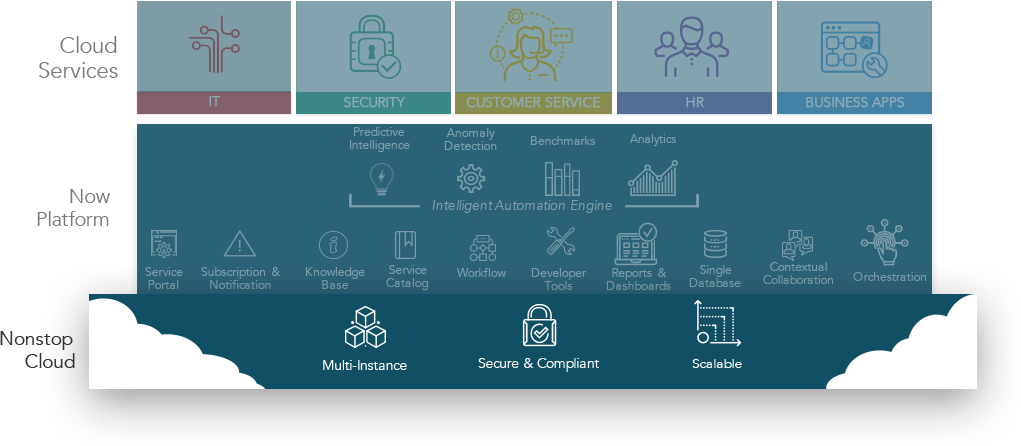
In a recent survey, over half of enterprises said they would choose cloud over on‑premises solutions. Significantly reduce infrastructure costs. Shift staff to innovation projects that benefit the business. And with Service Now, take advantage of our unique multi‑instance architecture, security protections, and high availability.
Multi-Instance Architecture
Free yourself from the restraints of multi‑tenancy. Our cloud infrastructure uses an advanced multi‑instance architecture so every customer gets its own unique application logic and database. Deploy and upgrade on your own schedule, customize your cloud services, and trust that your data is segregated from other customer instances.
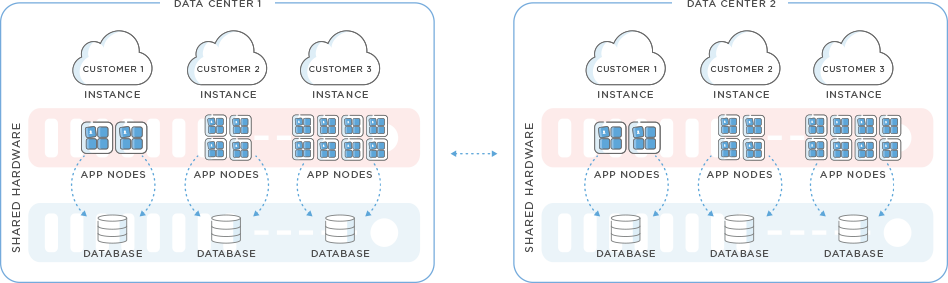
High-Availability Global Infrastructure
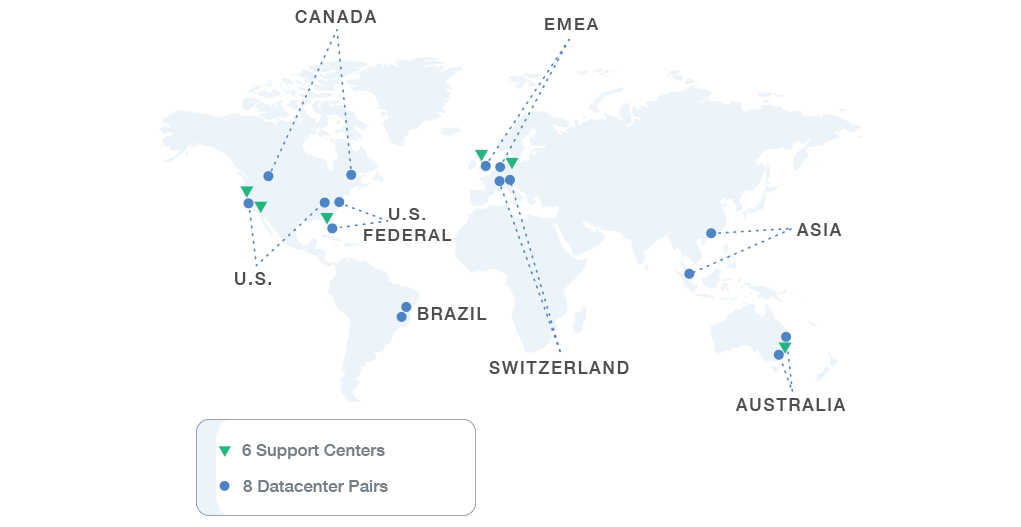
Our Nonstop Cloud is designed for Global 2000 enterprises in terms of availability, location, and scale. We run 8 pairs or 16 data centers across 5 continents to meet our customer’s physical location and data sovereignty needs. We focus on near‑perfect availability, own and operate all our data center equipment and hire full‑time data center employees.
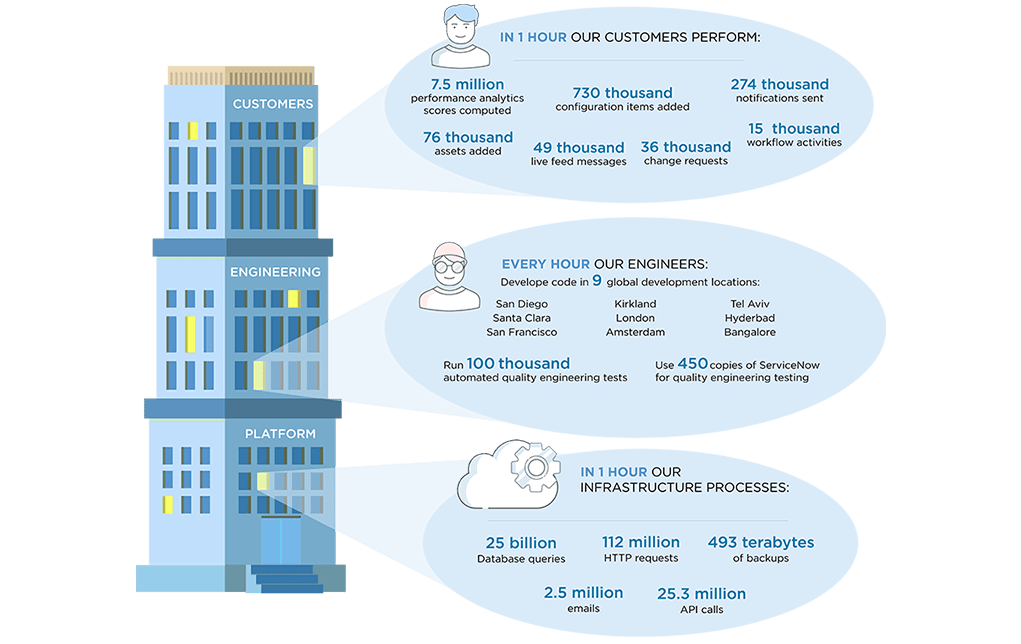
What Happens in an Hour on the Nonstop Cloud

We Are Committed to Delivering
Reliable and Secure Cloud Services
Earning and maintaining your organization’s trust is essential to building a lasting partnership. We believe that it is important to give you the utmost confidence in our ability to prevent and mitigate security threats, protect the privacy of your data, and help you comply with a growing number of global mandates. To this end, we have made significant investments in technology, processes, and expertise to ensure that our cloud services meet the most stringent of standards for performance, scalability, security, privacy, and compliance.
Operations and Availability
Your organization relies on access to IT and business data and services for its continued operation and success. Our Nonstop Cloud is designed to meet and exceed your high availability requirements and always be operational. We use the power and flexibility of the Now Platform to automate the provisioning, monitoring and scaling of our Nonstop Cloud. The production cloud environment is architected to host customer instances in region‑specific, geographically dispersed data center pairs that operate in an active‑active mode. Instance data is replicated in near real‑time. We provide the industry’s only Real Availability Dashboard that shows availability of all your instances running in the cloud. Our unique, multi instance architecture lets you fully customize your cloud services and perform upgrades on your own schedule.





